Welcome to the guide for setting up SSO and SCIM with Azure Active Directory (Azure AD) / Microsoft Entra ID (SAML-based) for your SiftHub account.
Why SSO?
Single Sign-On (SSO) integration allows your team to access SiftHub using their existing Azure AD credentials, eliminating the need for separate logins while ensuring secure access. This provides centralized authentication and enhanced security for your organization.
Why SCIM?
SCIM (System for Cross-domain Identity Management) automates user provisioning and management in SiftHub directly from your Azure AD dashboard. This means when you add, deactivate or update users in Azure AD, their SiftHub access is automatically managed, saving significant IT administration time.
Are both necessary?
While you can implement SSO without SCIM, we recommend using both for complete user lifecycle management. Here's what happens with SSO alone:
- Users can log in to SiftHub using Azure AD credentials
- BUT new users still need to be manually created in SiftHub as well as provisioned to access SiftHub in Azure AD
- When employees leave, their SiftHub accounts need manual deactivation
Using both SSO and SCIM automates the entire user lifecycle, from creation through updation to deletion, making it the recommended setup for enterprises.
This guide will walk through step-by-step instructions of how to set up SSO/SCIM using Azure AD for your SiftHub account.
Prerequisites
Before starting the setup, ensure you have:
- Global Administrator access to your Azure AD / Microsoft Entra ID account
- Access to the "Security" > "Authentication" section in the "Settings" panel of the SiftHub Account.
- This is usually visible to users having the 'Account Owner' and 'Security Admin' roles in SiftHub. If the Account Owner has Global Administrator access in Azure AD, they are equipped with the requisite permissions to complete the process.
- Otherwise, add the Azure AD administrator of your organization as a user in SiftHub with the Security Admin role.
- This user can be removed from SiftHub subsequently if you prefer so as to not consume an account license.
- Valid login credentials (email and password) for SiftHub. These will be deprecated once SSO with Azure AD is set up.
Step 1: Download Metadata XML from SiftHub
Start by getting the configuration details from SiftHub.
Log In to SiftHub
Log in to SiftHub as an Account Owner or Security Admin.
Navigate to SSO Setup
Go to Settings > Security > Authentication, then click Set up SSO.
Select Azure AD
Select Microsoft Entra ID, then SAML, and click Configure.
Download Metadata XML
Under Service Provider Details, click on Download Metadata XML. Save this file – you'll need it in the next step.
Step 2: Create Enterprise Application in Azure AD
Now, set up SiftHub as an application in your Azure AD portal.
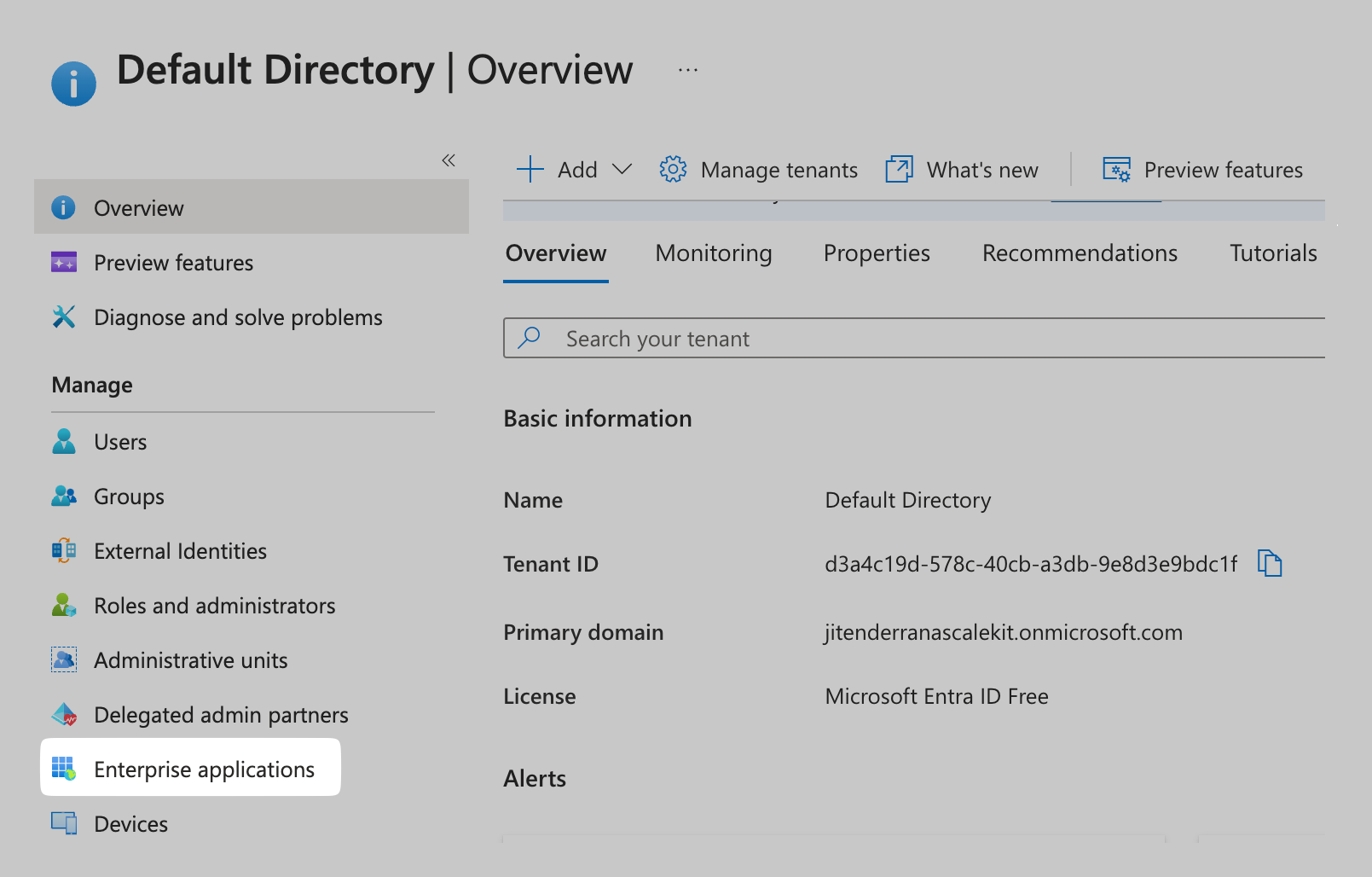
Log In to Azure Portal
Login to Microsoft Entra ID in the Microsoft Azure Portal. Select the option for Entra ID application and locate the Enterprise Applications tab.
Create New Application
In the Enterprise Applications tab, click New Application in the top navigation bar.
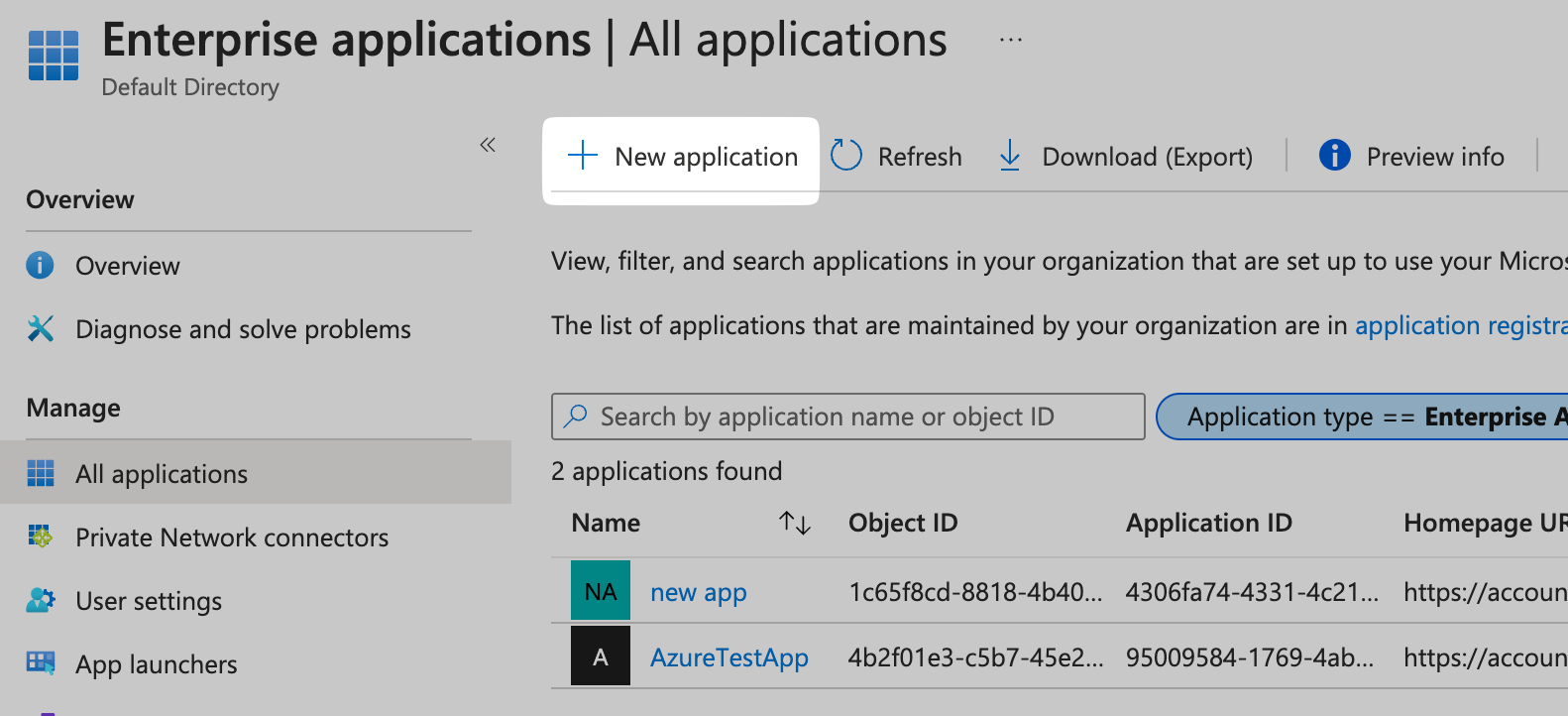
Create Your Own Application
Click on Create your own Application and give your application a name (e.g., "SiftHub SSO").
Select the Integrate any other application you don't find in the gallery (Non-gallery) option, then click Create.

Step 3: Configure SAML Settings
Configure the SAML connection between Azure AD and SiftHub.
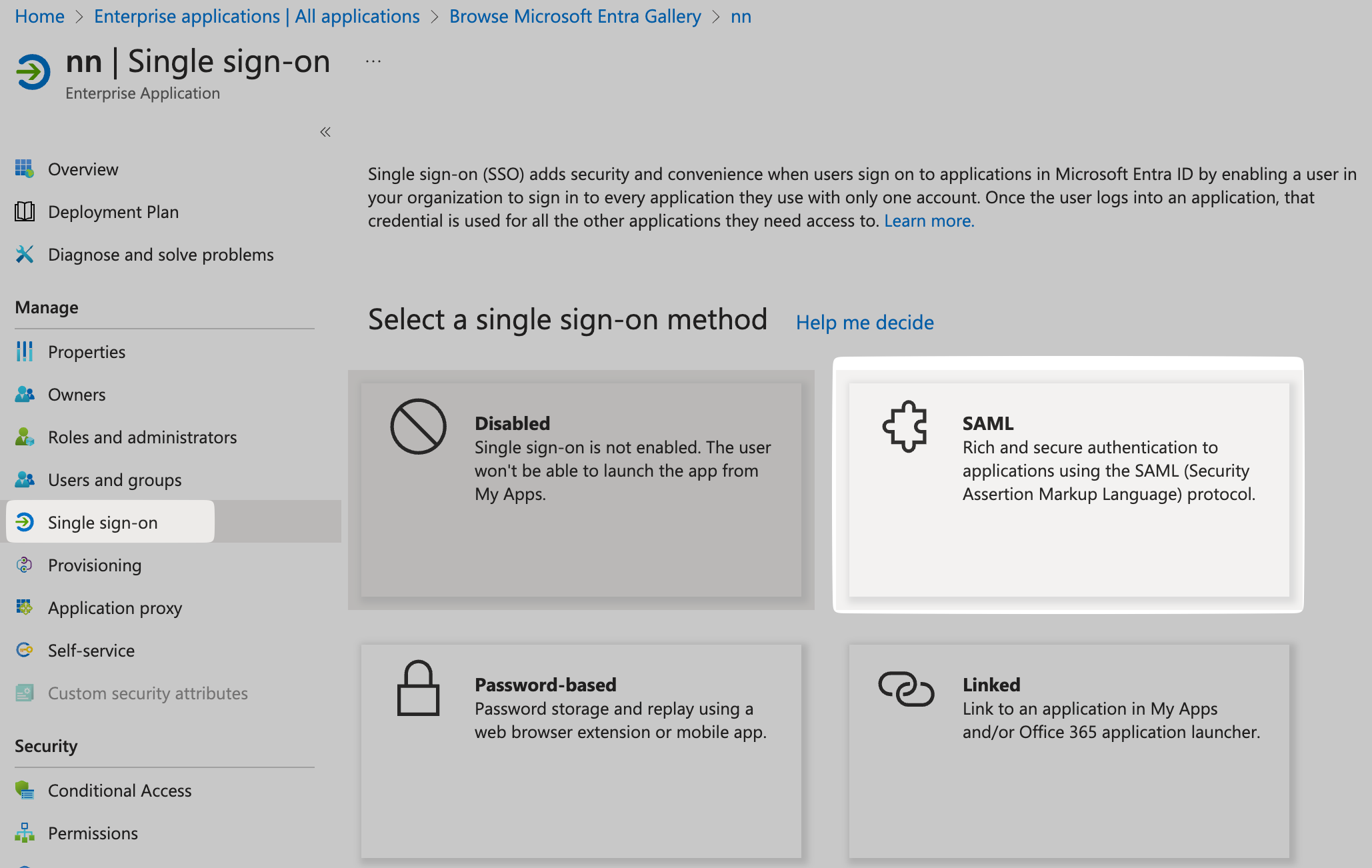
Open Single Sign-On Settings
Locate the Single Sign-On option under Manage, and choose SAML.
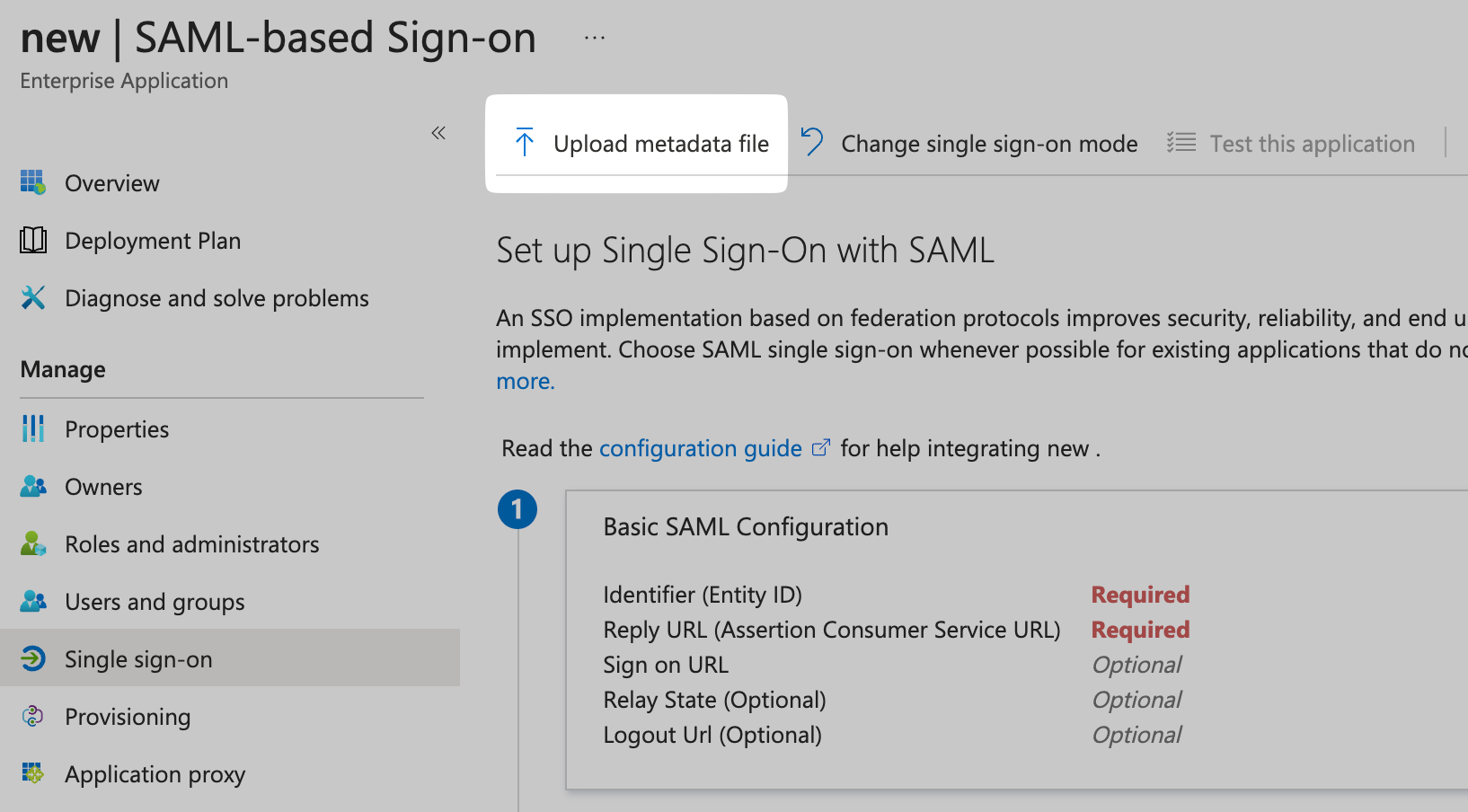
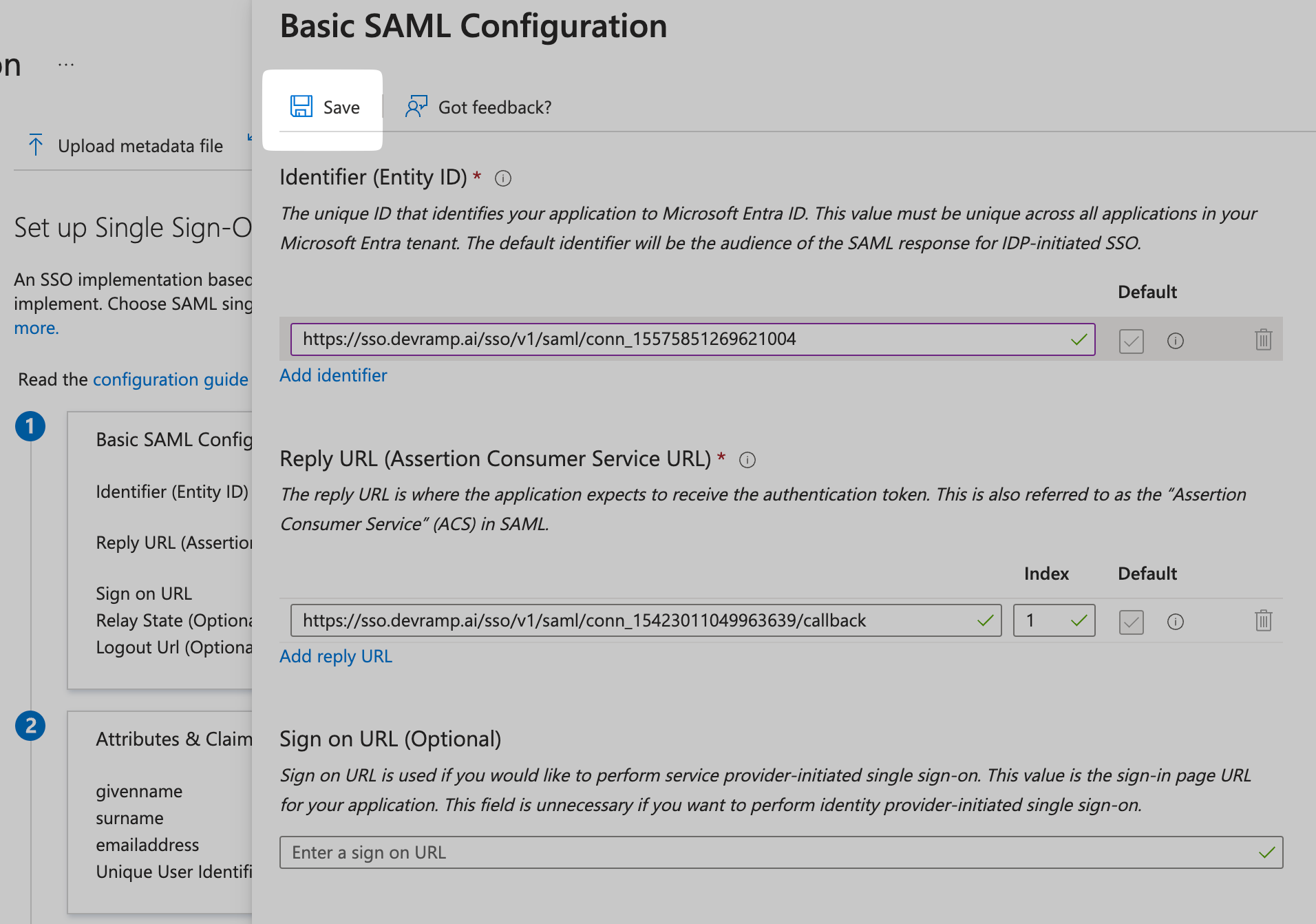
Upload Metadata File
Click on Upload metadata file. Upload the Metadata XML file you downloaded from SiftHub in Step 1.
Save Configuration
Click on Save.
Step 4: Map User Attributes
Ensure user information is correctly passed from Azure AD to SiftHub.
Edit Attributes & Claims
Under Attributes & Claims, click on Edit.
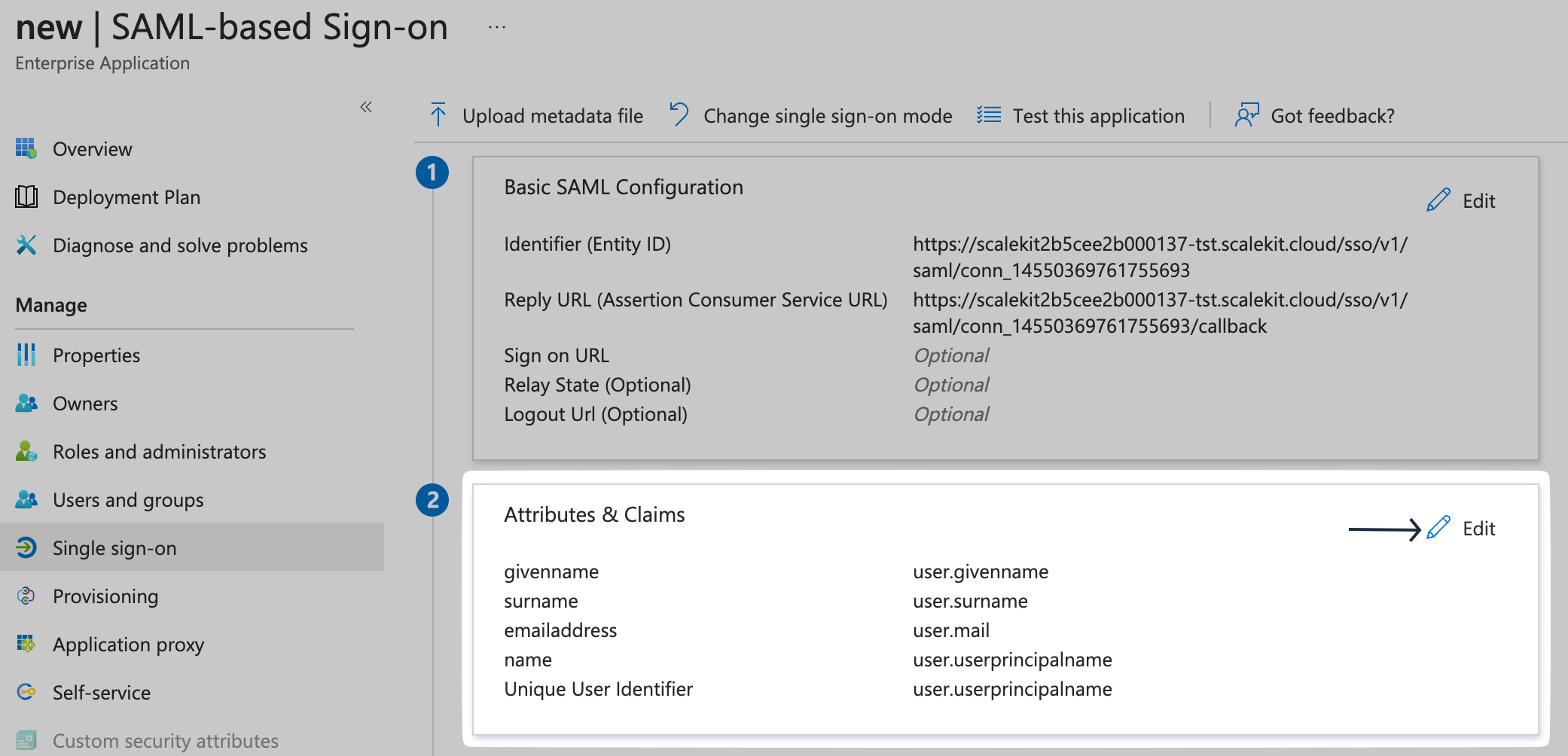
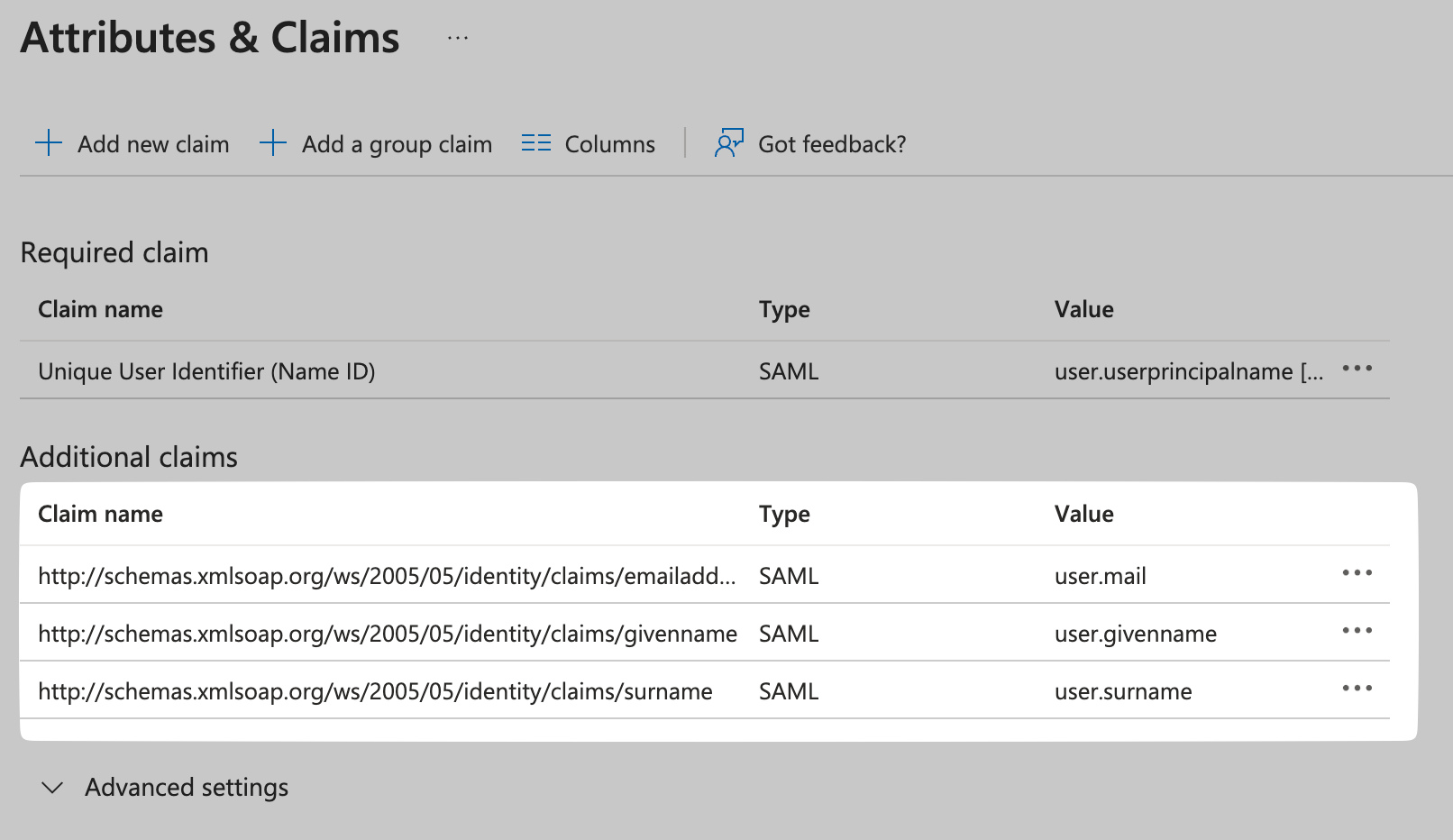
Configure Attribute Mapping
Check the Attribute Mapping section in the SSO Configuration Portal in SiftHub, and carefully map the same attributes in your Azure AD app.
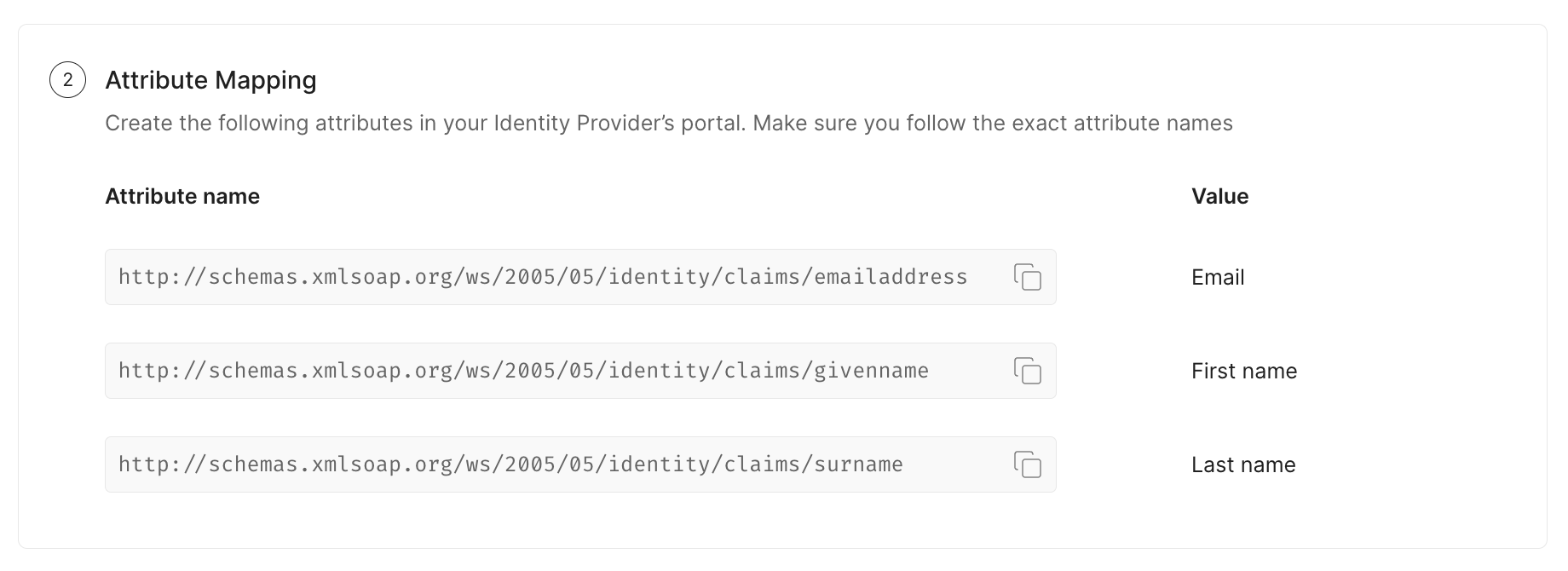
Typically, you'll need to map:
- email → user.mail (or user.userprincipalname)
- firstName → user.givenname
- lastName → user.surname
Step 5: Assign Users and Groups
Control who can access SiftHub via SSO.
Navigate to Users and Groups
Go to the Users and groups tab, and click on Add user/group.
Select Users or Groups
Select all the required users or user groups that need login access to SiftHub via Single Sign-On.
Step 6: Configure Metadata URL in SiftHub
Link Azure AD back to SiftHub to complete the connection.
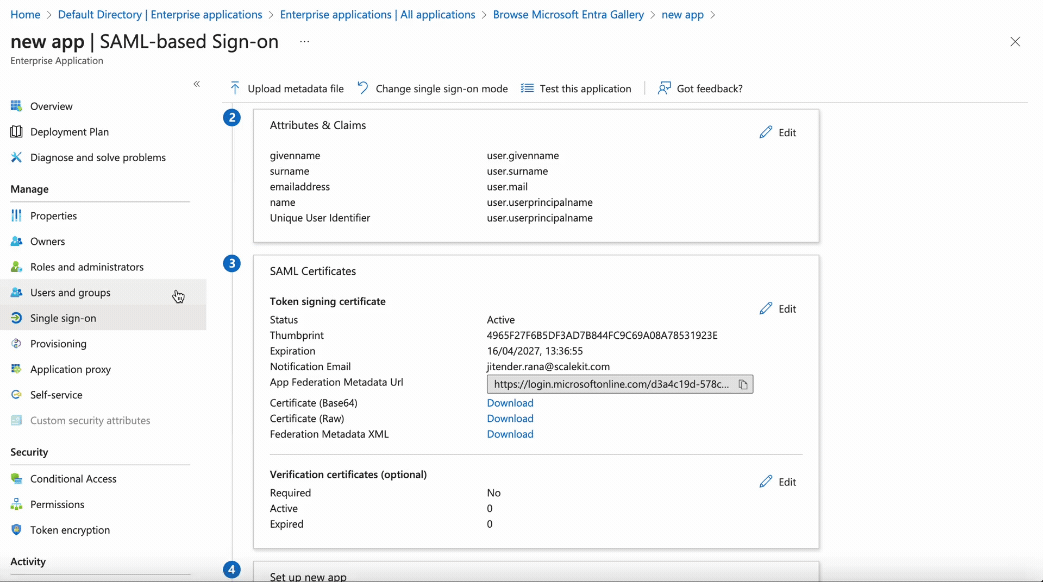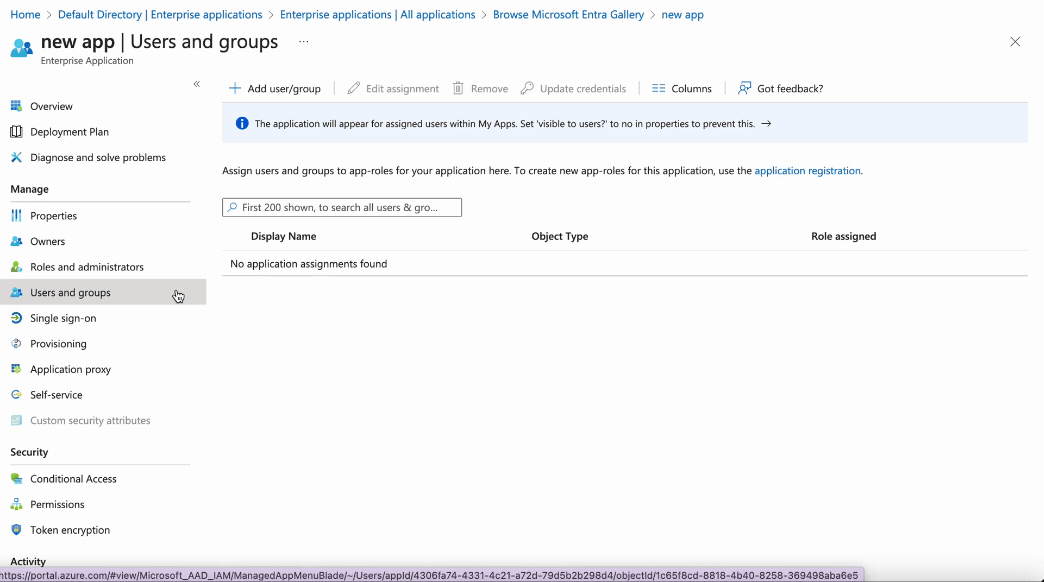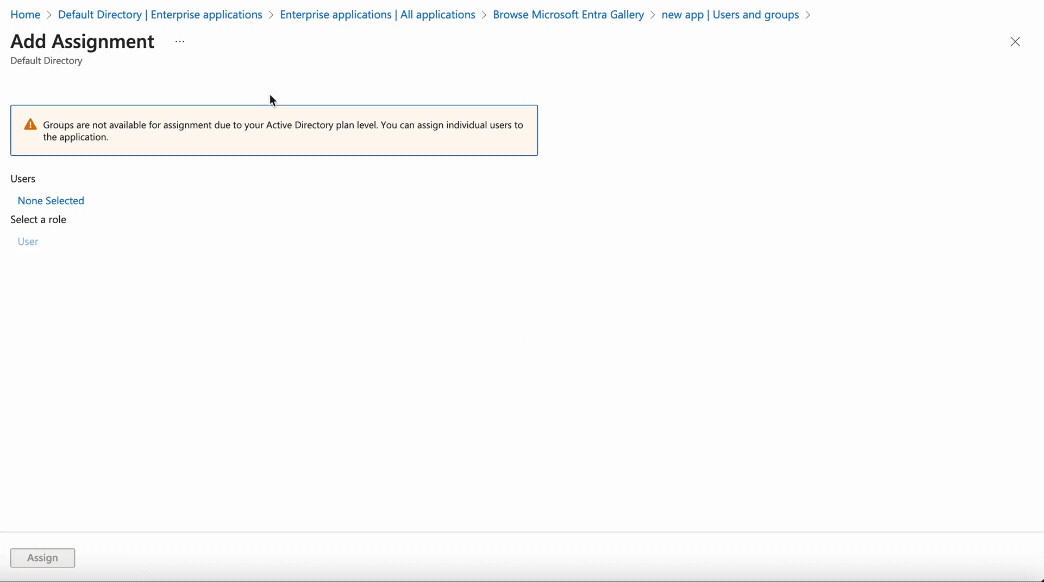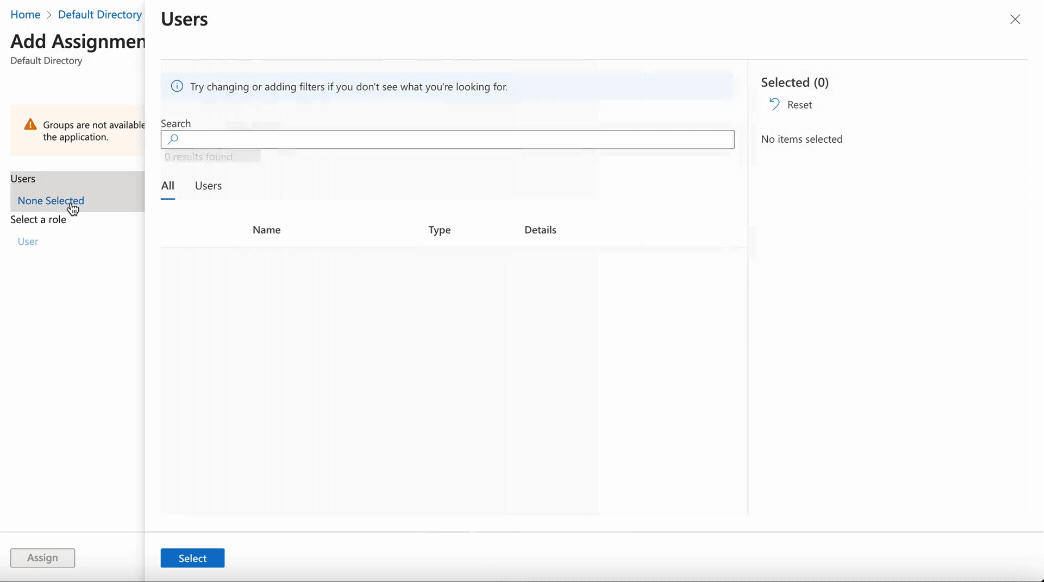
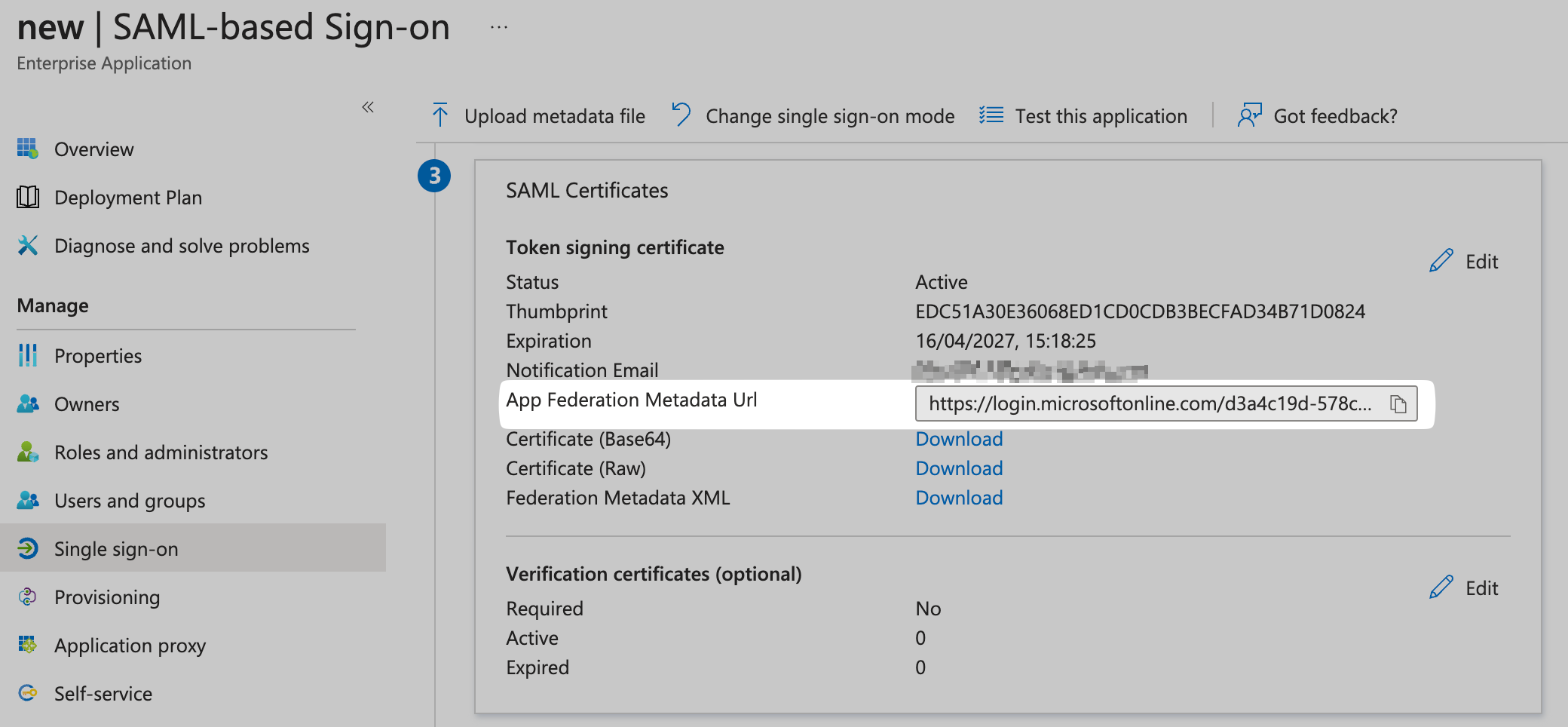
Copy Federation Metadata URL
In Azure AD, under SAML Certification, copy the link under App Federation Metadata URL.
Paste Metadata URL in SiftHub
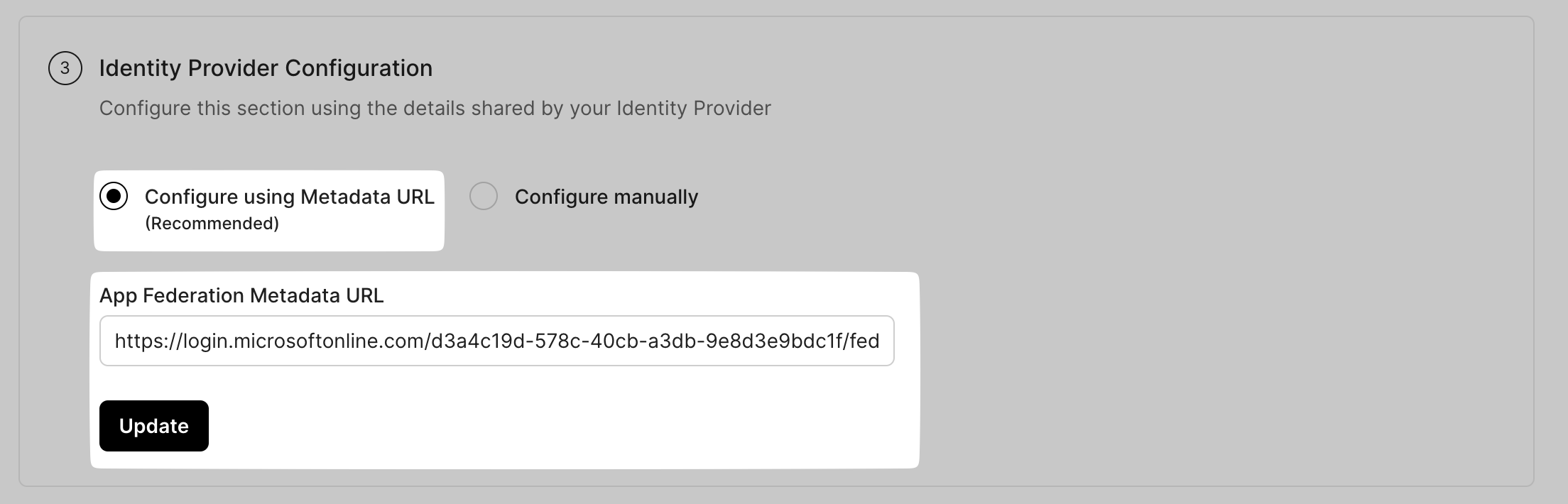
Return to SiftHub's Settings > Security > Authentication > Set up SSO page.
Under Identity Provider Configuration, select Configure using Metadata URL, and paste the App Federation Metadata URL you copied from Azure AD.
Step 7: Test the Connection
Verify that everything is configured correctly.
Run Connection Test
Click on Test Connection. If everything is done correctly, you will see a Success response.
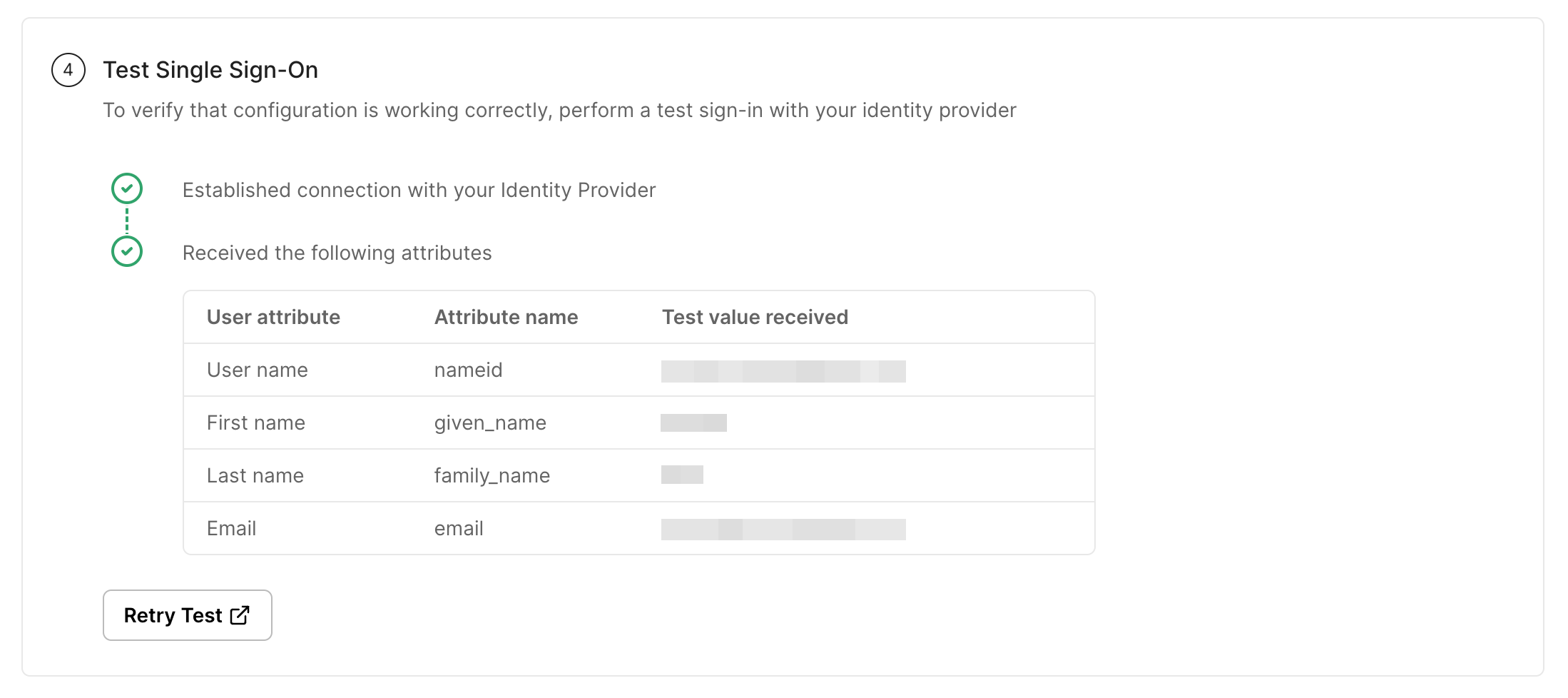
Note: If the connection fails, you'll see an error, the reason for the error, and a way to solve that error right on the screen.
Step 8: Enable the Connection
Activate SSO for your users.
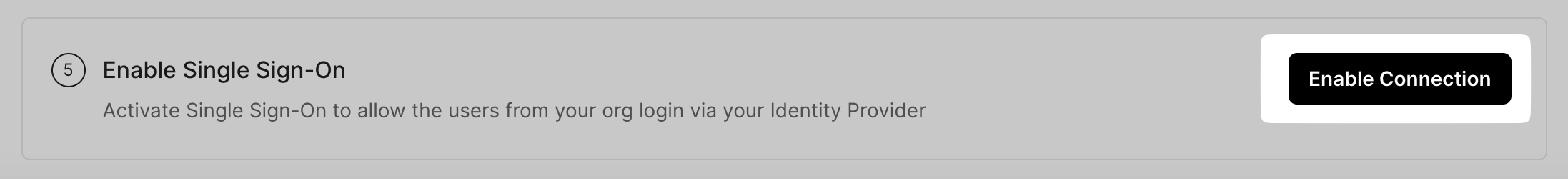
Enable SSO
Click on Enable Connection. This will allow all your selected users to log in to SiftHub via your Azure AD SSO.
Your team can now log in to SiftHub with their Azure AD credentials.
Need assistance? Contact your SiftHub Customer Success Manager!
All set with SSO? Proceed to the SCIM setup next!
Set Up SCIM with Azure AD
SCIM keeps your SiftHub user list in sync with Azure AD. Here's how to set it up:
Get Endpoint and Token from SiftHub
Start by generating the credentials Azure AD needs to sync with SiftHub.
Navigate to SCIM Setup
Log in to SiftHub as an Account Owner or Security Admin. Go to Settings > Security > Authentication, then click Set up SCIM.
Copy Directory Details
Under Directory Details, copy the Endpoint URL and Bearer Token. You'll need these in the next steps.
Add a New Application in Azure AD
Create a separate enterprise application for SCIM provisioning.
Navigate to Enterprise Applications
Go to the Microsoft Azure portal and select Microsoft Entra ID.
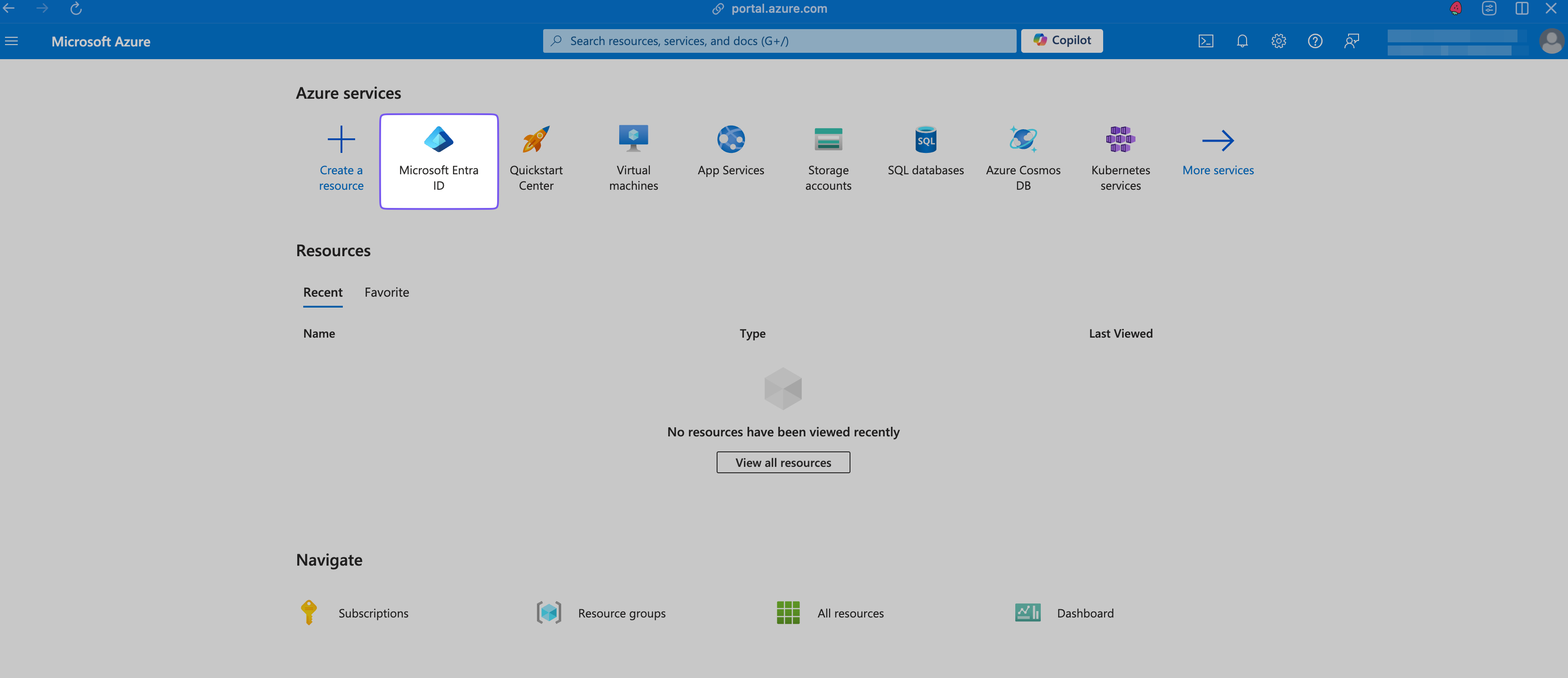
In the Manage > All applications tab, click + New application.
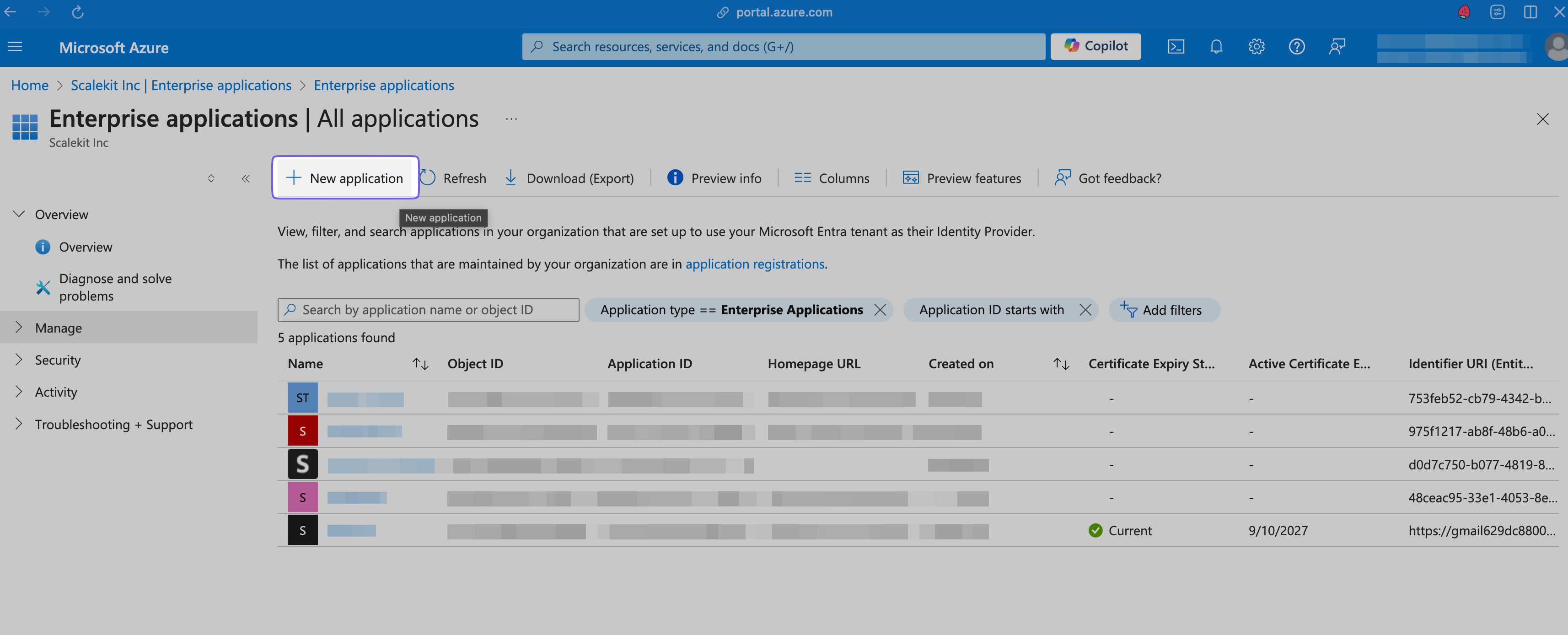
Create Your Own Application
Click + Create your own application in the modal that opens on the right.
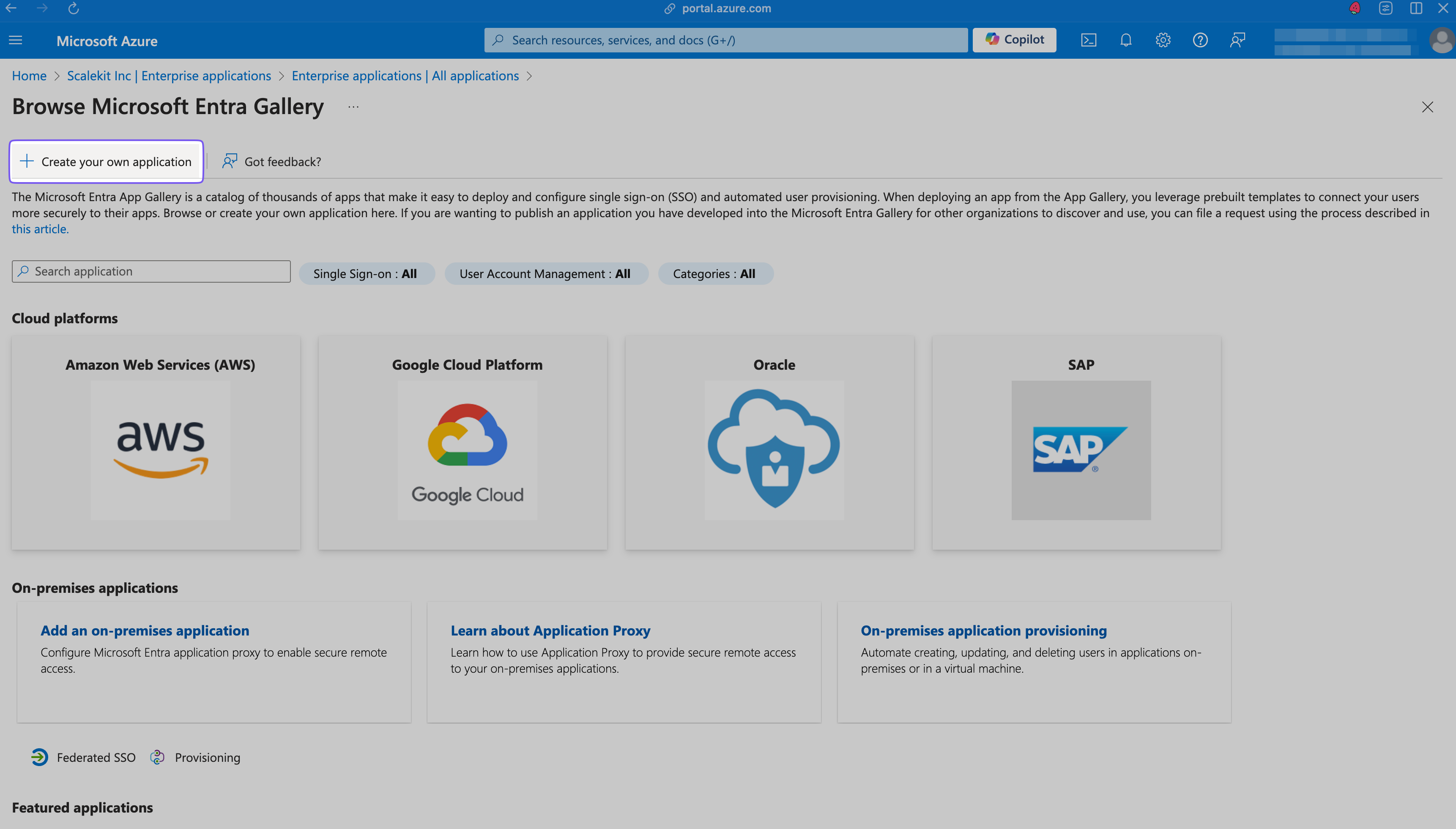
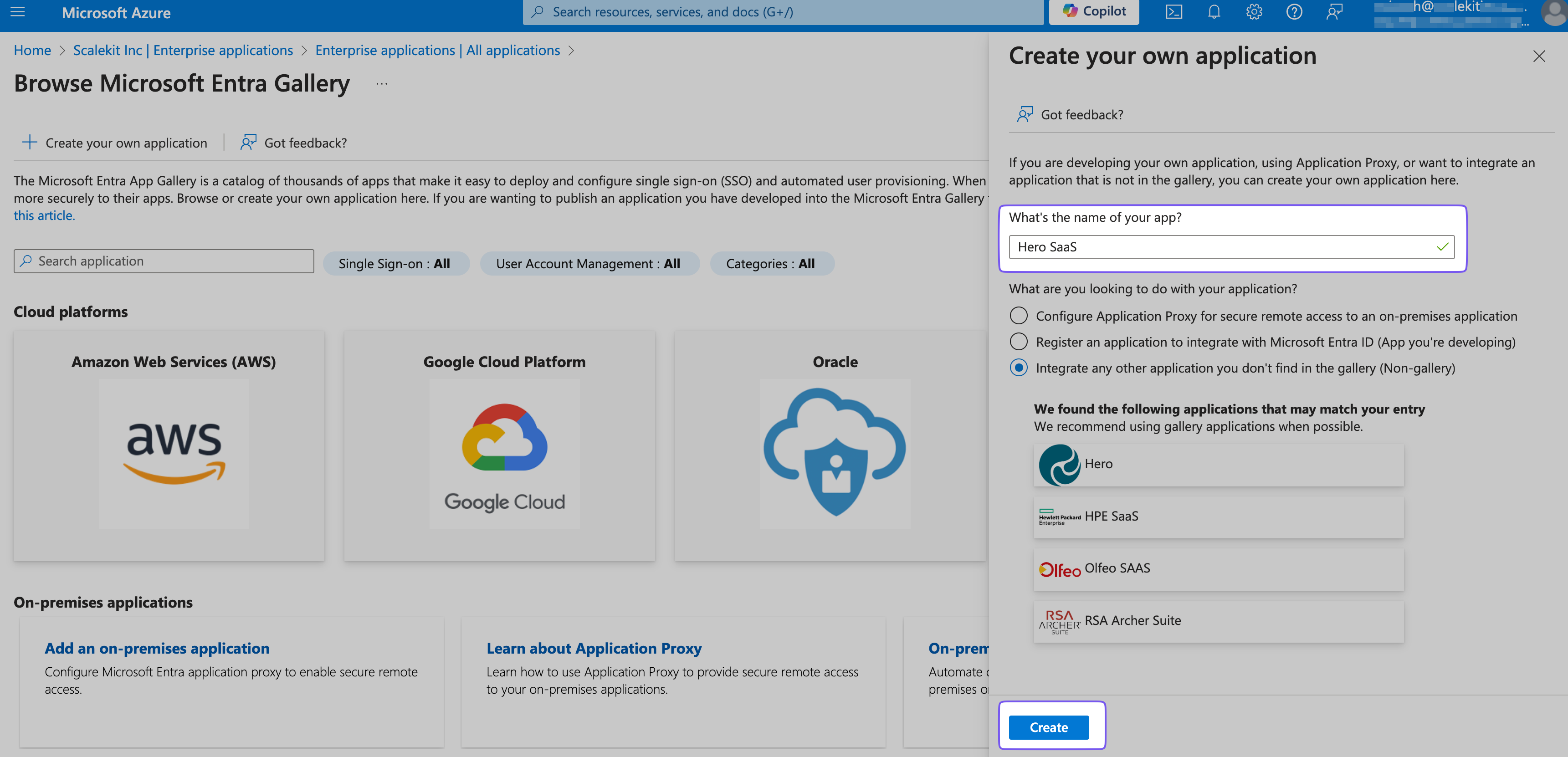
Name the Application
Name the app "SiftHub SCIM" (or similar) and click Create, leaving other defaults as-is.
Configure Provisioning Settings
Set up Azure AD to sync user data with SiftHub.
Open Provisioning Settings
In the "SiftHub SCIM" app's overview, select Manage > Provisioning from the left sidebar.
Set Provisioning Mode
Set the Provisioning Mode to Automatic.
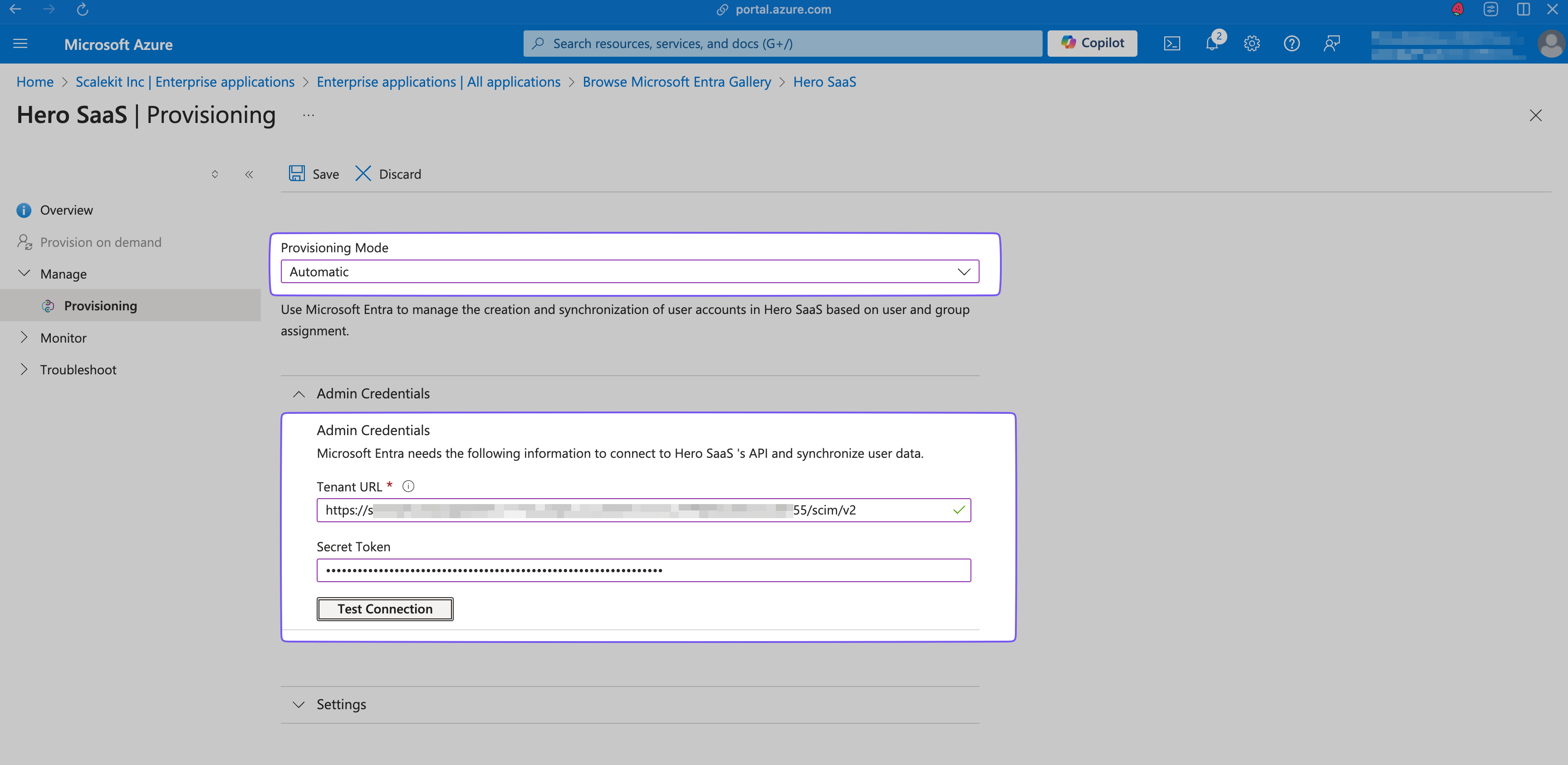
Configure Admin Credentials
In the Admin Credentials section, set:
- Tenant URL: Paste the Endpoint URL you copied from SiftHub
- Secret Token: Paste the Bearer Token you copied from SiftHub
Click Test Connection to verify the credentials work, then click Save.
Enable User Provisioning
Configure which user actions sync between Azure AD and SiftHub.
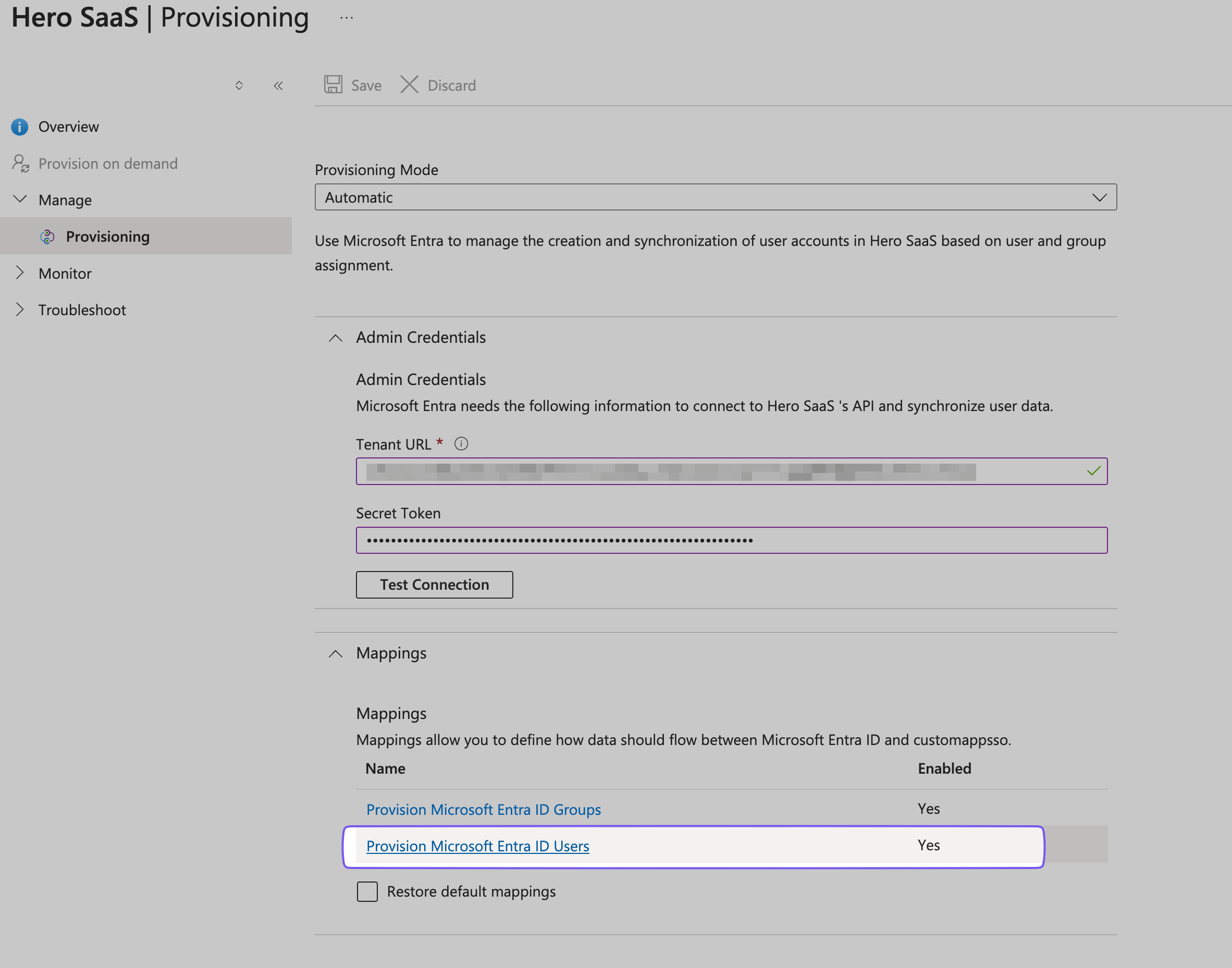
Configure User Mappings
In the Mappings section, click Provision Microsoft Entra ID Users and toggle Enabled to Yes.
Save and Reload
Close the modal and reload the page for changes to take effect.
Enable Provisioning Status
Go to Overview > Manage > Provisioning and ensure Provisioning Status is toggled On.
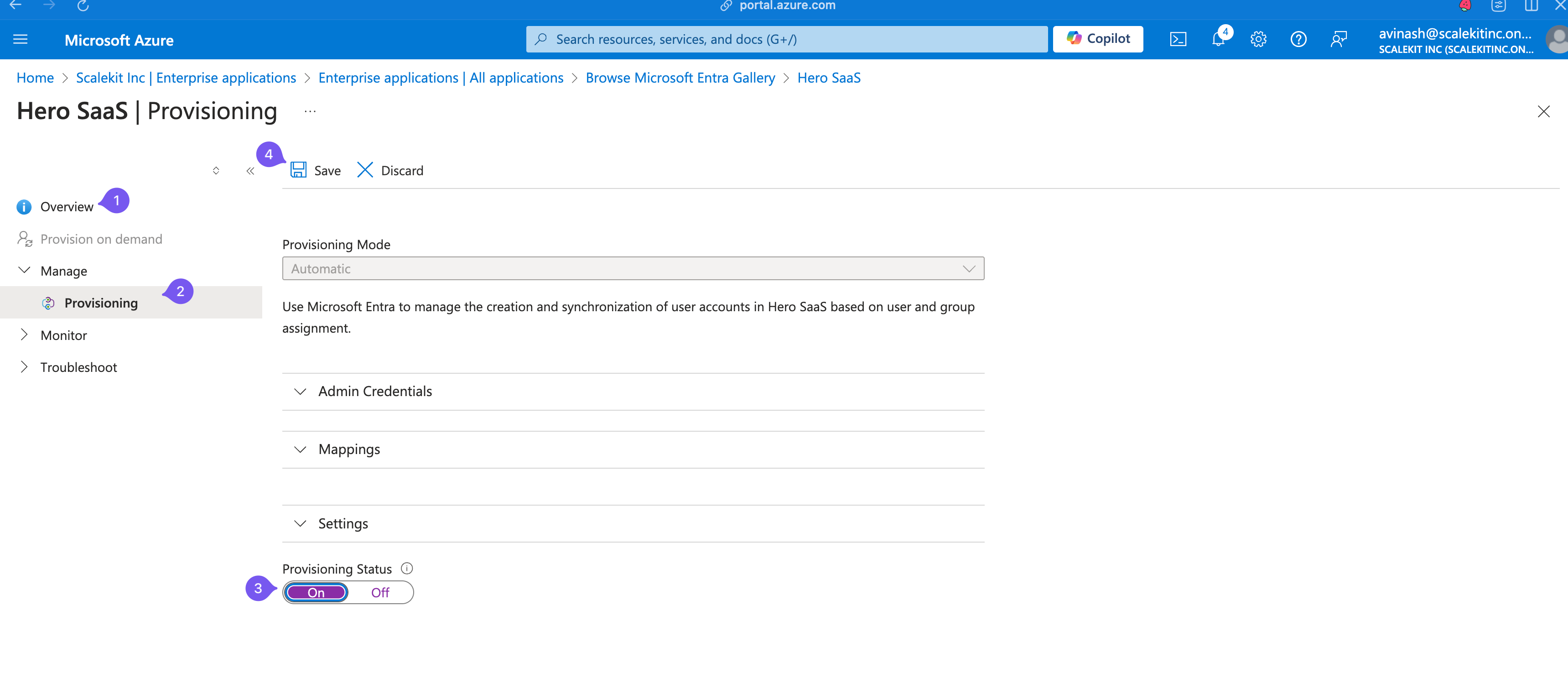
Azure AD is now set up to send events to SiftHub when users are added, updated, or removed.
Assign Users and Groups
Choose which users and groups to sync to SiftHub.
Navigate to Users and Groups
In the SiftHub SCIM application, go to Manage > Users and groups, then click Add user/group.
Select Users or Groups
Add the users or groups that should have access to SiftHub. These users will be automatically provisioned in SiftHub.
Test User Provisioning
Verify that provisioning works before rolling out to all users.
Provision On Demand
In the SiftHub SCIM application, go to Provision on demand. Input a user name from your user list and click Provision.
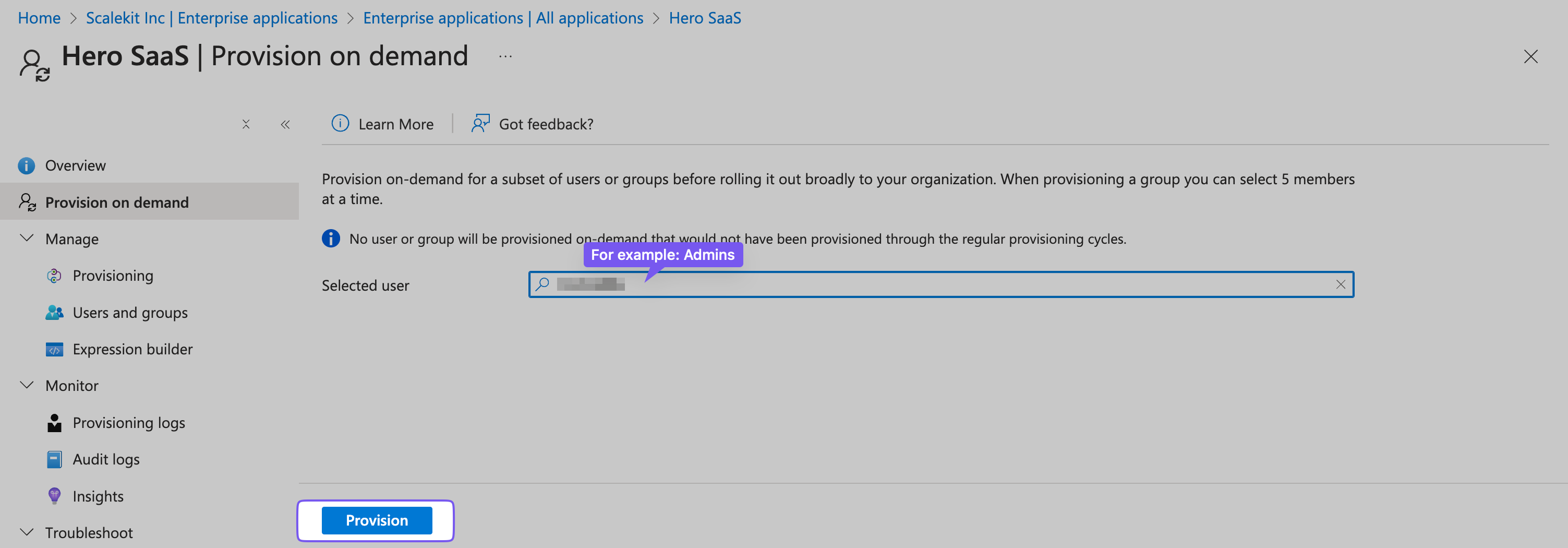
Verify in SiftHub
Once provisioned, the user should appear in SiftHub's Admin Portal under Settings > Users, confirming that provisioning is working correctly.
Note: Provisioning or deprovisioning users can be done from Manage > Users and groups > Add user/group. Azure AD takes up to 40 minutes for the changes to propagate to SiftHub.
All Done!
Your team can now log in to SiftHub with their Azure AD credentials, and user changes will sync automatically. Need assistance? Contact your SiftHub Customer Success Manager!